Seguridad en Expert Choice
En Expert Choice, la seguridad de la información es una prioridad. Estamos comprometidos en proteger los datos de nuestros clientes y garantizar la integridad de nuestros sistemas.
Certificación ISO 27001

Nos enorgullece estar certificados en ISO/IEC 27001:2022, un estándar internacional que establece los requisitos para un sistema de gestión de seguridad de la información efectivo. Esta certificación demuestra nuestro compromiso con la confidencialidad, integridad y disponibilidad de la información.
Nuestra casa certificadora es Normalización y Certificación NYCE, S.C., un organismo acreditado con el número 02/17 por la Entidad Mexicana de Acreditación A.C. (ema).
Certificado No. 2025CRI-366
- Fecha de emisión: 05 de marzo de 2025
- Vigencia hasta: 04 de marzo de 2028
- Alcance: Proceso de desarrollo y entrega de los servicios SaaS, así como el proceso de recabación, procesamiento, almacenamiento y entrega de informes de datos, de acuerdo con la Declaración de Aplicabilidad (SoA) ECH-DOC-SoA-V3 de fecha 27/02/2025.
Infraestructura Segura en AWS
Nuestra plataforma tecnológica se basa en Amazon Web Services (AWS), que cuenta con certificaciones reconocidas en el sector, como:
- PCI DSS nivel 1
- ISO 27001
- FISMA Moderate
- FedRAMP
- HIPAA
- SOC 1
Los centros de datos de AWS operan en múltiples zonas de disponibilidad a nivel mundial, garantizando una disponibilidad del 99.95% y una infraestructura de categoría Tier III+.
Seguridad en la Comunicación y Autenticación
Implementamos políticas y procedimientos alineados con nuestro Sistema de Gestión de Seguridad de la Información (SGSI) para garantizar la confidencialidad, integridad y disponibilidad de los datos:
- Cifrado y protección de datos: Aplicamos mecanismos de cifrado para proteger la información en tránsito y en reposo, asegurando comunicaciones seguras con nuestros clientes y proveedores.
- Autenticación y control de accesos: Seguimos un modelo basado en roles y permisos para garantizar que solo usuarios autorizados accedan a nuestros sistemas y aplicaciones.
- Gestión de riesgos: Contamos con un enfoque proactivo para la identificación, análisis y tratamiento de riesgos en la seguridad de la información.
- Monitoreo y respuesta a incidentes: Implementamos procedimientos de gestión de incidentes y auditoría para detectar y responder a posibles amenazas.
- Cumplimiento normativo: Nuestro SGSI abarca políticas y controles basados en estándares internacionales, asegurando que nuestras prácticas cumplan con las mejores recomendaciones en seguridad.
Mejores Prácticas en Seguridad
Adoptamos las mejores prácticas en seguridad tecnológica para proteger nuestros sistemas y datos:
- Autenticación multifactor (MFA): Añadimos una capa extra de seguridad requiriendo múltiples formas de verificación antes de otorgar acceso.
- Actualizaciones y parches regulares: Mantenemos nuestros sistemas actualizados para corregir vulnerabilidades conocidas.
- Cifrado de datos: Protegemos la información sensible mediante técnicas de cifrado tanto en reposo como en tránsito.
- Seguridad de redes: Implementamos medidas de segmentación y monitoreo de tráfico para prevenir accesos no autorizados y mitigar amenazas. Nuestros sistemas analizan continuamente el comportamiento de la red para detectar anomalías y responder de manera proactiva ante posibles incidentes.
- Capacitación continua: Formamos a nuestro personal en prácticas seguras de manejo de información y ciberseguridad.
- Gestión de accesos: Implementamos políticas estrictas para asegurar que solo personas autorizadas accedan a información sensible.
Desarrollo Seguro
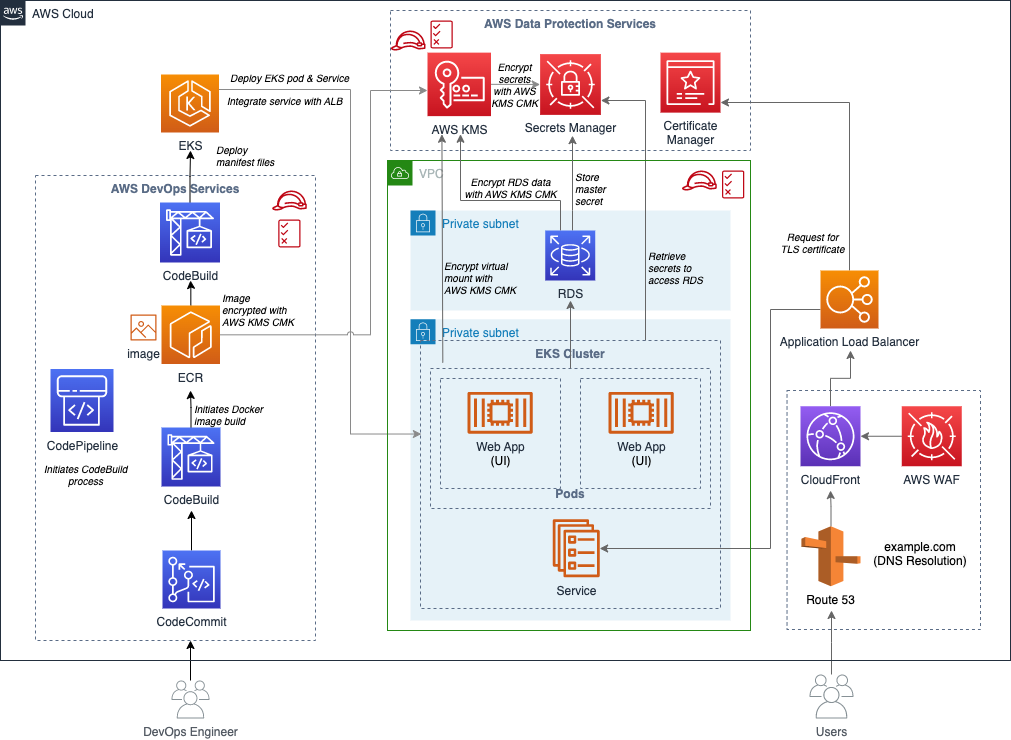
Nuestro equipo de desarrollo sigue los lineamientos del Open Web Application Security Project (OWASP) para garantizar la seguridad en nuestras aplicaciones. Esto incluye:
- Aplicación de las 10 principales vulnerabilidades OWASP para prevenir ataques comunes como inyección SQL, XSS y fallos en autenticación.
- Uso de prácticas seguras de codificación para evitar vulnerabilidades desde la etapa inicial del desarrollo.
- Pruebas de seguridad continuas en cada fase del ciclo de vida del desarrollo de software (SDLC).
- Auditorías y revisiones de código para detectar y corregir problemas de seguridad antes de la implementación.
- Implementación de Integración y Entrega Continua (CI/CD) para garantizar la automatización de pruebas y despliegues seguros.
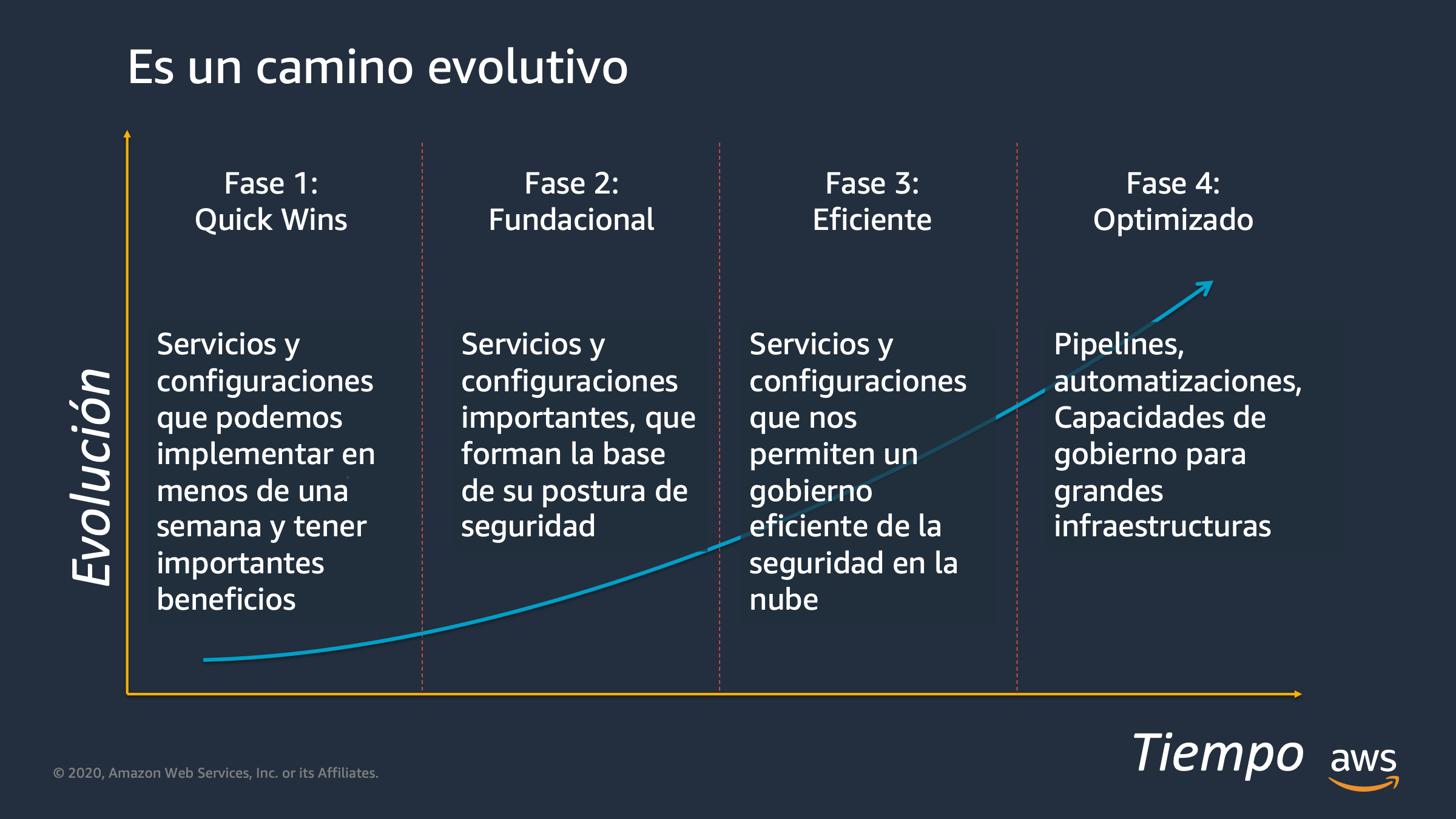
Compromiso con la Mejora Continua
En Expert Choice, nos comprometemos a evaluar y mejorar continuamente nuestras políticas y procedimientos de seguridad para adaptarnos a las amenazas emergentes y garantizar la protección de la información de nuestros clientes.
Para mayor transparencia, incluimos nuestro certificado de seguridad emitido por NYCE como respaldo de nuestro compromiso con la seguridad.






 Facebook
Facebook LinkedIn
LinkedIn Youtube
Youtube
